Bus services, city of Blaine brace for cuts after I-976 passes - Blaine Northern Light
Bus services, city of Blaine brace for cuts after I-976 passes - Blaine Northern Light |
- Bus services, city of Blaine brace for cuts after I-976 passes - Blaine Northern Light
- Horizontal Portal Market Research Report | Liferay Inc., Oracle Corporation, IBM Corporation - Sound On Sound Fest
- Hackers Can Use Lasers to ‘Speak’ to Your Amazon Echo or Google Home - WIRED
- Hackers Can Shine Lasers at Your Alexa Device and Do Bad, Bad Things to It - Popular Mechanics
| Bus services, city of Blaine brace for cuts after I-976 passes - Blaine Northern Light Posted: 26 Nov 2019 02:45 PM PST  Oliver Lazenby Local agencies aren't yet sure how the passage of Initiative 976, which caps car tab fees at $30, will affect Whatcom County transportation services and infrastructure, but they expect there will be some impacts. The initiative, passed statewide by voters with a 53 percent yes vote in the November election, repeals and reduces certain motor vehicle weight fees, repeals the authority for city transportation benefit districts to impose vehicle fees, reduces electric vehicle fees and repeals the 0.3 percent tax on motor vehicle retail sales, among other things. The Washington State Office of Financial Management told the Associated Press that the initiative could reduce state and local revenues by more than $4 billion over the next six years. In Whatcom County, the measure could potentially mean cuts to Whatcom Transportation Authority bus services, the Lummi Island ferry and funding for rural roadwork and other transportation projects. The city of Blaine has more than a dozen projects in its six-year Transportation Improvement Plan that rely at least partially on funding from state car tab fees, including sidewalks on Peace Portal Drive from F Street to Clark Street, resurfacing Semiahmoo Parkway and building another phase of the community trail along Peace Portal Drive south of Bell Road. The initiative's biggest impact is to the Bell Road grade separation project, "arguably the most significant public infrastructure project planned in the city for the next decade," according to a city council draft resolution opposing the initiative. That project would construct an overpass above the train tracks at Bell Road to alleviate traffic backups caused by passing trains. "We have $1.55 million in state funding for that that could be going away," said city public works director Ravyn Whitewolf. "It's all still up in the air. The state's also wrestling with what this all means so right now it's all kind of speculation." The city council had passed a resolution to oppose Initiative 976 at its October 28 meeting. The local impact of the initiative is not yet clear for several reasons. Seattle, King County and other agencies filed a lawsuit on November 13 that calls the initiative unconstitutional and requested an injunction on November 18 to stop it from going into effect until a judge can rule on the lawsuit. According to the plaintiffs, the initiative violates several provisions of the constitution by being misleading and by disallowing the tax to be used for voter-approved local projects. A court decision on the injunction was scheduled for Tuesday, November 26. Beyond that, much of the money the state collects from the fees goes into accounts that also get money from other sources. For example, car tab fees help fund the state's Rural Arterial Trust Account, which is also funded by fuel taxes and other sources. Since grants funded by the Rural Arterial Trust Account are not linked to specific funding sources within that account, it's not clear how the loss of one funding source will affect the program overall. Governor Jay Inslee directed the state department of transportation to postpone projects not yet underway and asked state agencies that receive funding from car tab fees to defer non-essential spending. Whatcom Transportation Authority could lose about $1 million per year for paratransit services – special needs transportation for the elderly and disabled. By state law, WTA is required to provide door-to-door transportation to riders whose disability prevents them from riding the fixed route bus system, so it cannot cut those services. For 2020, WTA can cover the loss of $1 million from its general fund or other funds, said spokesperson Maureen McCarthy. But in future years it may have to reduce fixed route services to make up for the loss, she said. "We are affected but not nearly as severely as some of our smaller transit peers," McCarthy said. For some rural bus services, a larger share of their operating revenue comes from state funds. The initiative could reduce transit services in Garfield County, in rural southeast Washington, by 50 percent, according to the Garfield County Transportation Authority. For car owners, the initiative goes into effect on December 6, according to the Washington State Department of Licensing. Whatcom County residents pay the base rate of $68.25 for cars under 4,000 pounds. That includes a $30 renewal fee, a $4.50 filing fee to the county and $8.75 in service fees, plus a vehicle weight fee of $25 for cars under 4,000 pounds. Elsewhere in the state, car tabs can cost more than $200. Other counties or cities may have higher fees due to local transportation benefit districts that fund transportation projects. (The city of Blaine has a transportation benefit district that is funded through a local sales tax and does not affect car tab fees.) Residents of King, Pierce and Snohomish counties pay a regional transit authority tax to Sound Transit. Seattle is likely the most expensive place in the state to renew vehicle tabs. Residents there pay the base fee of $68.25, an additional $80 fee for the city's transportation benefit district that funds maintenance and safety enhancements and a fee to Sound Transit that varies based on vehicle value that could cost an extra $150 for a six-year old car with a $24,000 original retail price, according to the state department of licensing office's fact sheet on car tabs. Political activist Tim Eyman sponsored Initiative 976. He's been working on similar car tab initiatives since about 1998, according to a January 2000 Seattle Times article. |
| Posted: 27 Nov 2019 03:07 AM PST New York City, NY: Nov 27, 2019 – Published via (Wired Release) – MarketResearch.Biz report on the Horizontal Portal Market is an important tool for market stakeholders in their quest to discover entrance for innovation, and further undertake business strategic planning for the launch of new products and services. The research study report we offer on the Horizontal Portal Market serves as a useful guide for market vendors. The report insights about demand growth drivers, challenges, threats, risks and opportunities that are likely to influence the Horizontal Portal market over the forthcoming period. These market stakeholders help businesses pave way in a crowded business scenario, and way ahead in the competition with full confidence. Study of worldwide Horizontal Portal market current and future trends and projections of yearly annual growth rates (CAGRs) for 2019 to 2028 are the key highlight of this report. It also shed light on the coverage of growing funding and investments for Horizontal Portal market research and development along with the description of major advancement, growth drivers and innovation and regional dynamics, latest trends within the industry. Further, the Horizontal Portal market report serves solid groundwork and reveal data of markets share of vital segments of the Horizontal Portal market under product, typr, application, and region. To ascertain market indicators, Horizontal Portal marketers employed validate research tools and capability for the same. The analysis of Horizontal Portal market indicators guide business carry out the most strategic planning for competitive profit. These indicators also guide marketers gauge investment proposition and scope of growth in the Horizontal Portal Market over the forecast period. For Better Understanding, Download Free Sample PDF Brochure of Horizontal Portal Market Research Report @ https://marketresearch.biz/report/horizontal-portal-market/request-sample The scope of this market report is thorough and covers solution type, application, and region of Horizontal Portal market. The market has been segmented by key players into: com Inc., Oracle Corporation, Liferay Inc., Episerver, Backbase, Hippo B.V, Kentico Software, Jahia Solutions Group SA, IBM Corporation, Adobe Systems Inc. and Sitecore Global horizontal portal market segmentation by solution type: Software, Services. Global horizontal portal market segmentation by application: Telecom and IT, Healthcare, Military, Automotive, Consumer Electronics, Other The report also comprise a discussion of the major competitiors in the Horizontal Portal market across each region: United States, Europe, China, Japan, Southeast Asia, India, Central & South America. Furthermore, know detail of competitive outlook, the Horizontal Portal market report includes SWOT analysis of leading players, and how this will affect the competitive scenario until the end of the forecast period 2019-2028. This serves as a vital Horizontal Portal market intelligence indicator to indicate growth strategies adopted by market stakeholders, and their pose on Horizontal Portal mergers, acquisitions, collaborations and partnerships that can help remain their position in the market competition. Any Query? Fill Free To Inquire Here. We'll Put You On The Right Path: https://marketresearch.biz/report/horizontal-portal-market/#inquiry Scope of The Market: Firstly, the report segments the Horizontal Portal market with respect to solution type, application, and region. In the segmentation study, key segments are studied based on Horizontal Portal market share, size, production, consumption, revenue(volume), size, CAGR value and other factors linked with the market. Revenue projection for the defined period are given for individual segment and region-wise Horizontal Portal market, with a projected value obtain from the revenue of market vendors complete revenues. Further, it explain the Horizontal Portal market major growth drivers, innovations, technological development and regional dynamics, as well as recent and upcoming trends within the Horizontal Portal industry. The Horizontal Portal market report will guide you to understand the various types of products that are presently in use and the variants estimated to achieve prominence in the future. The Report Would Help New Entrants and Marketers In The Following Ways: -It helps in understanding the complete growth of the Horizontal Portal market. It also offers data about key Horizontal Portal market drivers, restraints, challenges, threats, risks and opportunities. It provides the closest estimation of the Horizontal Portal revenue for the complete market and its sub-segments. -The study also gives the positioning of the leading players based on their business strategies and product offerings. It helps market stakeholders to understand their competitors better and gaining more details to strengthen their positions in the top of the market. -It helps you to understand the most impacting driving and constraining forces in the Horizontal Portal market and its effect on the market globally. Browse Full Summary of Horizontal Portal Market Enabled with Respective Tables and Figures at: https://marketresearch.biz/report/horizontal-portal-market/ Moreover, through the statistical study, the Horizontal Portal market report depicts the worldwide industry comprising production value, cost/profit, capacity, production, supply and demand, and import and export. Moreover, the Horizontal Portal market report serves crucial strategic initiatives taken by leading players operating in the market along with ranking study for the prominent players. Thanks for reading this article; we can also provide individual chapter wise or region wise section report version like North America, Europe or Asia, Latin America Middle East & Africa according to your requirement. Contact Us: Mr. Benni Johnson Prudour Pvt. Ltd. 420 Lexington Avenue, Suite 300 New York City, NY 10170, United States Tel: + 1-347-826-1876 Email ID: inquiry@marketresearch.biz Website: https://marketresearch.biz/ |
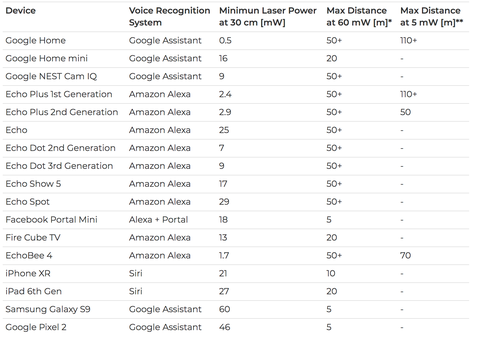
| Hackers Can Use Lasers to ‘Speak’ to Your Amazon Echo or Google Home - WIRED Posted: 04 Nov 2019 12:00 AM PST  In the spring of last year, cybersecurity researcher Takeshi Sugawara walked into the lab of Kevin Fu, a professor he was visiting at the University of Michigan. He wanted to show off a strange trick he'd discovered. Sugawara pointed a high-powered laser at the microphone of his iPad—all inside of a black metal box, to avoid burning or blinding anyone—and had Fu put on a pair of earbuds to listen to the sound the iPad's mic picked up. As Sugawara varied the laser's intensity over time in the shape of a sine wave, fluctuating at about 1,000 times a second, Fu picked up a distinct high-pitched tone. The iPad's microphone had inexplicably converted the laser's light into an electrical signal, just as it would with sound. Six months later Sugawara—visiting from the Tokyo-based University of Electro-Communications—along with Fu and a group of University of Michigan researchers have honed that curious photoacoustic quirk into something far more disturbing. They can now use lasers to silently "speak" to any computer that receives voice commands—including smartphones, Amazon Echo speakers, Google Homes, and Facebook's Portal video chat devices. That spy trick lets them send "light commands" from hundreds of feet away; they can open garages, make online purchases, and cause all manner of mischief or malevolence. The attack can easily pass through a window, when the device's owner isn't home to notice a telltale flashing speck of light or the target device's responses. "It's possible to make microphones respond to light as if it were sound," says Sugawara. "This means that anything that acts on sound commands will act on light commands." In months of experimentation that followed Sugawara's initial findings, the researchers found that when they pointed a laser at a microphone and changed the intensity at a precise frequency, the light would somehow perturb the microphone's membrane at that same frequency. The positioning didn't need to be especially precise; in some cases they simply flooded the device with light. Otherwise, they used a telephoto lens and a geared tripod to hit their mark. As a result, the microphone interpreted the incoming light into a digital signal, just as it would sound. The researchers then tried changing the intensity of the laser over time to match the frequency of a human voice, aiming the beam at the microphones of a collection of consumer devices that accept voice commands. When they used a 60 milliwatt laser to "speak" commands to 16 different smart speakers, smartphones, and other voice activated devices, they found that almost all of the smart speakers registered the commands from 164 feet away, the maximum distance they tested. Smartphones proved trickier: An iPhone was only susceptible from a range of around 33 feet, and two Android phones could only be controlled from within around 16 feet. |
| Hackers Can Shine Lasers at Your Alexa Device and Do Bad, Bad Things to It - Popular Mechanics Posted: 06 Nov 2019 12:00 AM PST
Keep Alexa away from all windows: Turns out hackers can shine lasers at your Google Assistant or Amazon Alexa-enabled devices and gain control of them, sending commands to the smart assistants or obtaining your valuable account information. Researchers proved this by using lasers to inject malicious commands into voice-controlled devices like smart speakers, tablets, and phones across long distances through glass windowpanes. In a new paper, "Light Commands: Laser-Based Audio Injection Attacks on Voice-Controllable Systems," the authors describe the laser-based vulnerability as a "signal injection attack" on microphones based on the photoacoustic effect, which converts light to sound through a microphone. From the abstract:
User authentication is lacking or nonexistent on voice assistant devices, the researchers also found. That meant they could use the light-injected voice commands to unlock the victim's smartlock-enabled doors, shop on their e-commerce sites, use their payment methods, or even unlock and start vehicles connected to the victim's Google account. The research—funded by the Japan Society for the Promotion of Science and the U.S. Defense Advanced Research Projects Agency (DARPA), among other organizations—was meant to uncover possible security vulnerabilities in Internet of Things devices. "While much attention is being given to improving the capabilities of [voice controlled] systems, much less is known about the resilience of these systems to software and hardware attacks," the authors write in the paper. "Indeed, previous works already highlight a major limitation of voice-only user interaction: the lack of proper user authentication." So how does it work? The mics can convert sound into electrical signals, sure, but they also react to light aimed directly at them. By using a high-intensity light beam, modulating an electrical signal, the researchers could trick the microphones embedded in the voice devices into producing electrical signals as if they were receiving real audio from your voice, for example. That means hackers can then inject inaudible commands through the light beams. Devices are vulnerable from up to 110 meters away, as of the time of the paper's publication. That's about the length of a football field. Pretty much any voice-enabled device you can imagine is vulnerable to this kind of attack, but the authors have tested and confirmed vulnerabilities in the following: Perhaps the most disturbing part is how easy this kind of hack is. All you need, according to the research group, are a simple laser pointer, a laser diode driver (which keeps a constant current of power supply to the laser), a sound amplifier, and a telephoto lens to focus the laser better for long-range attacks. While this research and the associated hacks were conducted by professional researchers, criminals could do the same (though they found no instances of this happening maliciously ... yet). However, with the methodology out there now, it's a double-edged sword: Yes, some consumers may read about this vulnerability and prepare against it, but now hackers also have new ideas. It's pretty difficult to tell if you're being attacked this way, but users may notice the light beam's reflection on the device in question or a user can try to monitor the device's verbal response and light pattern changes. If you notice your device acting erratically, more or less, unplug the damn thing and move it away from the window. The good news is that there are ways to protect yourself from a laser-based attack, according to the paper:
|
| You are subscribed to email updates from "portal sound effect" - Google News. To stop receiving these emails, you may unsubscribe now. | Email delivery powered by Google |
| Google, 1600 Amphitheatre Parkway, Mountain View, CA 94043, United States | |








Comments
Post a Comment